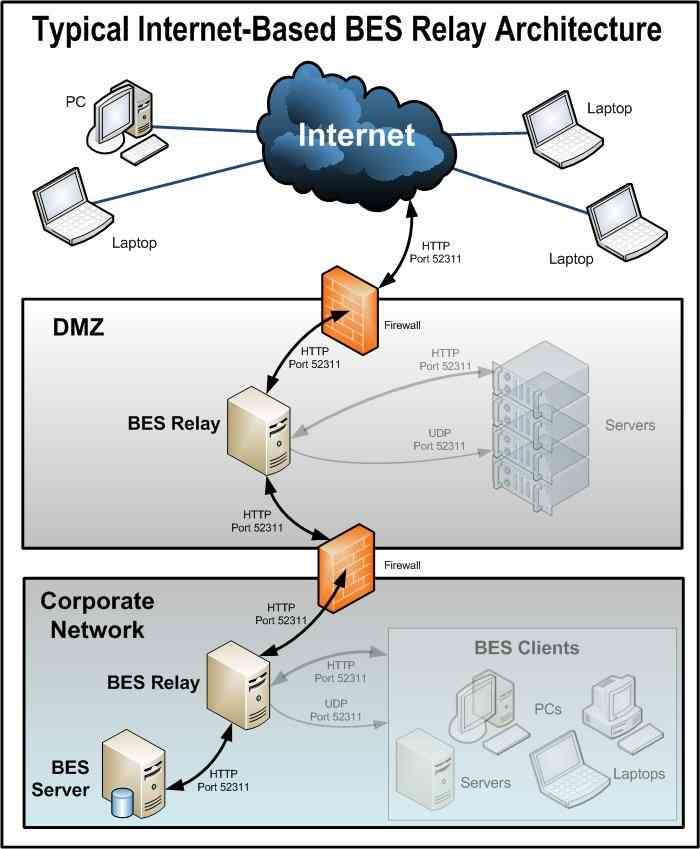
With BigFix, you can easily set up a relay on your DMZ to do everything they do as if they were on the network. By opening a port and making a few configuration changes, this is possible. Regardless of whether you are in a domain or on the internal network, BigFix can help manage devices securely over the internet. Following is a guide on how quickly you can get this set up.
For advanced configurations, see https://help.hcltechsw.com/bigfix/9.5/platform/Platform/Installation/c_relays.html.
- Create a DNS alias for the name of your DMZ relay.
- Open port 52311 and ICMP traffic from your external firewall to your DMZ relay defined within your DMZ.
- Install BigFix Relay on the machine that lies in your DMZ.
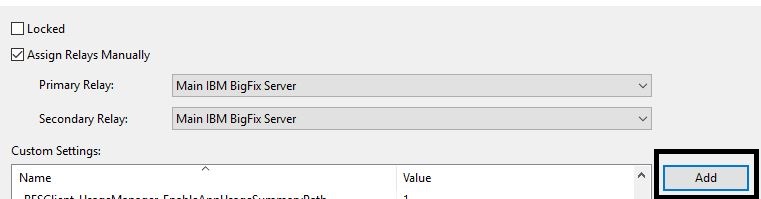
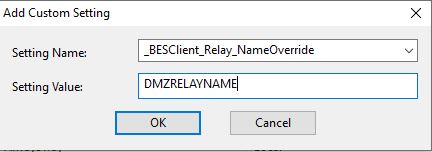
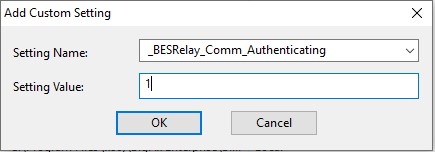
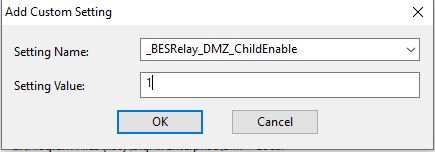
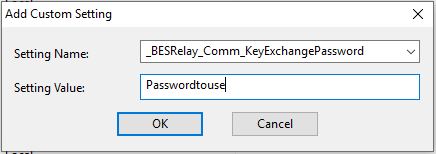
- Add client settings to the DMZ relay machine.
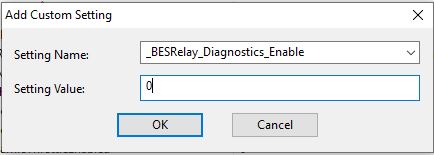
This disables the relay diagnostics page.
This setting allows you to enter a common name for the relay and not the actual PC name. It is the same name you set in the DNS alias earlier.
This only allows trusted agents to gather content or post reports. For details, see https://help.hcltechsw.com/bigfix/9.5/platform/Platform/Console/AuthenticatingRelays.html#Authenticatingrelays
This step enables persistent connections on the DMZ relay since UDP is often unreliable in DMZ. Enable _BESRelay_DMZ_ParentEnable on the relay the DMZ relay communicates to.
For details, see https://help.hcltechsw.com/bigfix/9.5/platform/Platform/Config/c_persistenconn2.html
Another setting that adds an additional level of security, so only devices with this password can register is the following: _BESRelay_Comm_KeyExchangePassword
Note: The client must have the _BESClient_SecureRegistration client setting with the corresponding password in order to register. For details, see https://help.hcltechsw.com/bigfix/9.5/platform/Platform/Console/ManualKeyExchange.html#Manualkeyexchange
- Open the BESAdmin tool on your BigFix server.
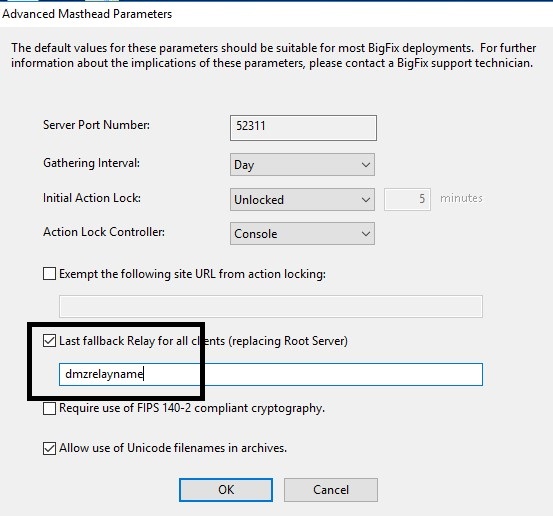
- Add your DMZ relay information to the Last fallback relay for all clients (replacing the root server) parameter. This updates the masthead and if they are unable to resolve the main BigFix server, they fallback to the DMZ relay for communication.
Note: Add the DNS name or the alias and nothing else for the fallback.
Note: This fallback relay needs to be resolved both internally and externally.
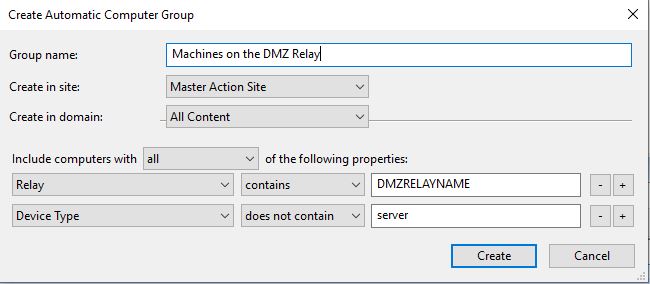
- Create an automatic group for clients connecting to the DMZ relay.
- Create a new automatic group with the relay property that contains your DMZRELAYNAME (replace with the friendly name you set earlier).
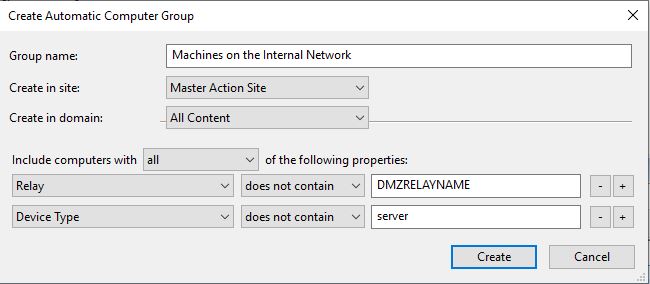
- Create a group for the clients on your internal network.
- Set up internal client settings that tell it to communicate with the DMZ relay when its off the network
Deploy the following settings to your clients on the DMZ:
- _BESClient_Comm_CommandPollIntervalSeconds
- _BESClient_Comm_CommandPollEnable
- _BESClient_RelaySelect_FailoverRelayList
Since UDP is often blocked through DMZ, the settings enable the BigFix agent to check in every 30 minutes through command polling. The failover list indiates to the client if it cannot resolve a relay. It then fails over to the relays on the list.
Following is an example of a client settings policy you can deploy to your machines on your DMZ: https://bigfix.me/fixlet/details/26677
- replace the relevance in expression 3 with your DMZRELAYNAME
- replace the relevance in expression 4 with your DMZRELAYNAME
- edit the action script along with the corresponding relevance statement in the action script with your DMZRELAYNAME.
This will be deployed to the group created earlier - “Machines on the DMZ relay”
- Set up a policy once they come back on the network. These settings change back for internal communications so that it polls every 12 hours and not 30 minutes.
- _BESClient_Comm_CommandPollIntervalSeconds
- _BESClient_Comm_CommandPollEnable
Following is a guide on how to create client settings policies: https://www.linkedin.com/pulse/bigfix-tune-control-your-client-fit-needs-brad-sexton/
- replace the relevance in expression 3 with your DMZRELAYNAME
- replace the relevance in expression 4 with your DMZRELAYNAME
- edit the action script along with the corresponding relevance statement in the action script with your DMZRELAYNAME
This will be deployed to your machines in the group created earlier - “Machines on the internal network”
These actions will change the settings for how the agent performs on the DMZ and then once the computers come back on the internal network switch back. This will help them perform efficient both internally and externally.
Once your relay is set up, you can then use your DMZ relay for your mergers and acquisitions. You could create a relay on a separate network and then have that relay communicate with your DMZ relay regardless of what domain your machines are in the network. For more information on how to set up and use your DMZ relay for mergers and acquisitions, refer to this post: https://www.linkedin.com/pulse/bigfix-use-mergers-acquisitions-brad-sexton/
~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
Author
Brad Sexton is a BigFix technical advisor for the mid-Atlantic region. He was a BigFix administrator in a global enterprise for 7 years where he was using BigFix for OSD, Software Deployments, and patching. Brad joined the HCL BigFix team in 2018.
Review and editorial credits
Shivi Sivasubramanian is a senior-level technical author and editor with a demonstrated history of working in the technology industry. A firm believer in the magical power of words, she loves helping the community deliver expressive, minimalist, and user-friendly content. Shivi currently leads a team of information developers in BigFix.