With great power comes great responsibility! While having domain admin rights on your workstation, you do not want to log in to it and use it to check your email or do your day-to-day activities. The same goes with your BigFix Master Operator. Your Master Operator account is needed for configuring your environment; your day-to-day job of patching and pushing out software should be used with a least privileged one. For details, see my earlier article on how to set up roles and grant your account the access privileges it needs. You can also set additional security controls in your accounts. For details, see the official documentation.
In this article however, I will walk you through the steps for setting up some of these features to keep additional checks in place so they fit your organizational needs.
- On your BigFix Server computer, open BigFix Administration Tool (BESAdmin).
- Enter the site key and password when prompted.
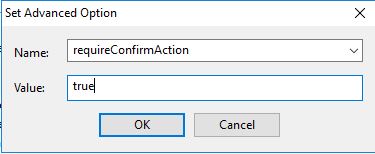
- Open the Advanced Option tab and select Add.
The first setting to add is requireConfirmAction - set the value to true and click OK.
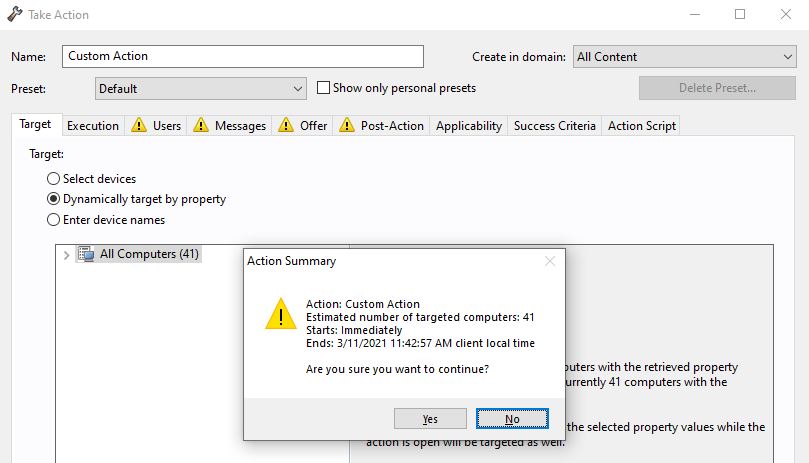
A summary of the action is displayed. Click OK to proceed.
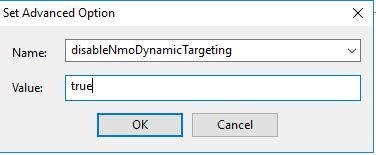
disableNmoDynamicTargeting
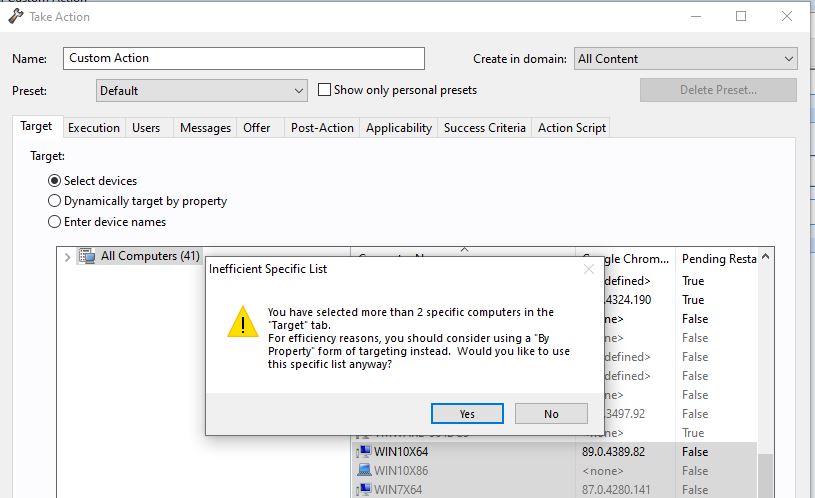
This action prevents non-master operators (NMO) from targeting dynamically and sending out mass deployments. It only allows them to target either by using a list or by entering the device names manually.
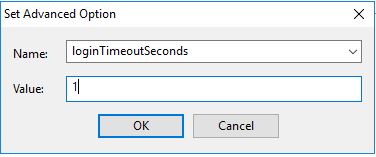
loginTimeoutSeconds
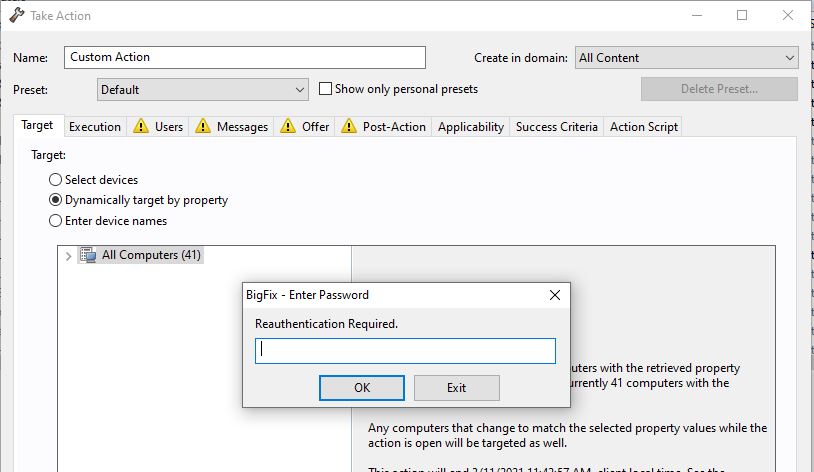
This forces the operator including master operators to re-authenticate before each action is taken.
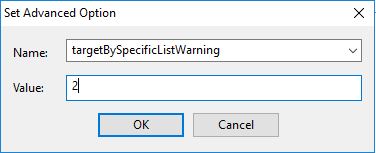
targetBySpecificListWarning
This issues a warning to the console operator when they target more machines than a predefined value.
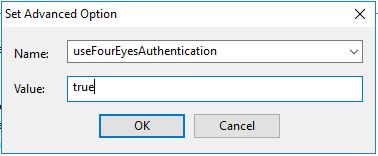
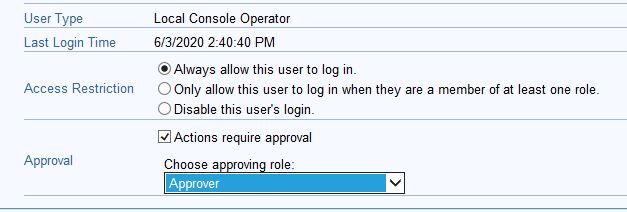
useFourEyesAuthentication
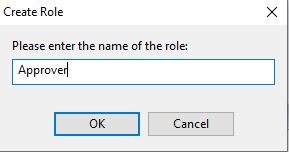
- Go to roles settings and create an "approver" role and add the operators you want to be able to approve actions.
- Set the operator that you want to be able to force an approval before the actions can be run.
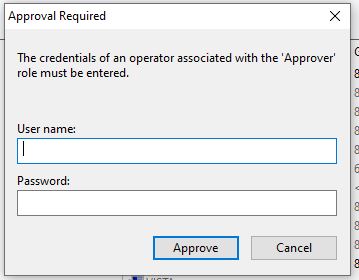
Once this is done, you are prompted to enter the approver's credentials before taking an action.