Main features of BigFix Version 9.5.6
The main features of this release include:
- Resigning of Mac Clients with new certificates
- Console Qualification for Windows 10 Creators Update
- Security enhancements
- APAR and defect fixes
Get more information by reading the full technical changelist at: https://support.bigfix.com/bes/changes/fullchangelist-95.txt
Things to take into account before upgrading to Version 9.5.6
If you are upgrading from a pre-9.5.5 version, please ensure you have a look at the following sections of the BigFix 9.5.5 Releases Notes:
Things to take in account before upgrading to Version 9.5.5
System requirements for Version 9.5.5
Those same considerations apply to 9.5.6 as well.
Other things to know about version 9.5.6
Relay Diagnostic changes.
Starting from 9.5.6 the Relay Diagnostic page on both Server and Relay components is disabled by default. After the upgrade, the Relay Diagnostic page cannot be accessed from a browser without explicitly being enabled.
The following message will be returned trying to access the Relay Diagnostic page:
RelayDiagnostics is not enabled.
To enable RelayDiagnostics and optionally set a password to protect the page, see BigFix Official Documentation.
The Relay Diagnostic page can be re-enabled by configuring each Server and/or Relay with the client setting _BESRelay_Diagnostics_Enable = 1
While re-enabling the Relay Diagnostic page, you can optionally decide to password-protect the page. To configure and require a Relay Diagnostic page password, you can use the new client setting _BESRelay_Diagnostics_Password.
NOTE: Changing _BESRelay_Diagnostics_Password requires a relay restart to be effective.
OpenSSL Initialization changes.
Starting from 9.5.6, each BigFix component initializes OpenSSL in FIPS Mode based on the value configure in the following priority:
First, the value of the client setting _BESClient_Cryptography_FipsMode is used. If the above setting does not exist, then the value of require-fips-cryptography set in the client's deployment masthead is used. If the client masthead is not found, Web Reports only will also check the masthead in its install folder. Finally, if both the client setting and the masthead are missing, OpenSSL is initialized with FIPS Mode enabled.
For reference, the location of the client's deployment masthead referenced above is defined as follow:
- Windows: registry key KLM\SOFTWARE\Wow6432Node\BigFix\EnterpriseClient\GlobalOptions\StoragePath
- Linux: environment variable BESClientActionMastheadPath.
New masthead parameter: minimumSupportedClient.
9.5.6 introduces a new masthead parameter: minimumSupportedClient. The purpose of this parameter is to enforce a higher level of security in the deployment. For this release, minimumSupportedClient can assume two values which are 0.0 and 9.0.
- 0.0 - The Server maintains compatibility with components at versions prior to 9.0.
- 9.0 - The Server will discard any unsigned reports. All clients in the deployment MUST be at 9.0 or higher which send signed reports.
You can use the BESAdmin tool to update or set this new masthead parameter, with the following syntax:
On Windows:
BESAdmin.exe /minimumSupportedClient=<VALUE> /sitePvkLocation=<LICENSE_PVK_FILE> /sitePvkPassword=<LICENSE_PVK_PWD>
On Linux:
/opt/BESServer/bin/BESAdmin.sh -minimumSupportedClient=<VALUE> -sitePvkLocation=<LICENSE_PVK_FILE> -sitePvkPassword=<LICENSE_PVK_PWD>
where <VALUE> can be set to 0.0 or 9.0
Currently, it is not possible to use the BES Admin tool to read this setting once set. To check it, look in the masthead file for the following line:
x-bes-minimum-supported-client-level: <VALUE>
NOTE:
- Any clients at version 8.2 or lower in the deployment will stop working as soon as minimumSupportedClient is set to 9.0.
- If the parameter is missing in the masthead or exists with a value less then 9.0, it is equivalent to setting the value 0.0.
- A BigFix 9.5.6 fresh installation, using a new License Authorization file, will automatically set this parameter to 9.0. BigFix 9.5.6 fresh installs using a masthead or license file, and any upgrade to 9.5.6 will not set this parameter.
New masthead parameter: minimumSupportedRelay.
9.5.6 introduces a new masthead parameter: minimumSupportedRelay. The purpose of this parameter is to enforce a higher level of security in the deployment. For this release, minimumSupportedRelay can assume two values which are 9.5.6 and 0.0.0
- 0.0.0 - The Server maintains compatibility with relays at versions prior to 9.5.6.
- 9.5.6 - The Server & Relays will always enforce HTTPS communications from Relays and Clients for registration requests. All relays in the deployment MUST be at 9.5.6 or higher AND all clients in the deployment MUST be at 9.0 or higher which support secure registration.
NOTE: This parameter should only be set to 9.5.6 if all the Servers and Relays in the deployment are already at level 9.5.6 or higher AND all the Clients are at 9.0 or higher. If this is not the case, setting this parameter can result in Clients not properly registering with their Relays and overloading the Server.
You can use the BESAdmin tool to update or set this new masthead parameter, with the following syntax:
On Windows:
BESAdmin.exe /minimumSupportedRelay=<VALUE> /sitePvkLocation=<LICENSE_PVK_FILE> /sitePvkPassword=<LICENSE_PVK_PWD>
On Linux:
/opt/BESServer/bin/BESAdmin.sh -minimumSupportedRelay=<VALUE> -sitePvkLocation=<LICENSE_PVK_FILE> -sitePvkPassword=<LICENSE_PVK_PWD>
where <VALUE> can be set to 0.0.0 or 9.5.6
Currently, it is not possible to use the BES Admin tool to read this setting once set. To check it, look in the masthead file for the following line:
x-bes-minimum-supported-relay-level: <VALUE>
NOTE:
- Any clients at version 8.2 or lower in the deployment will stop being able to send registration requests as soon as minimumSupportedRelay is set to 9.5.6.
- If the parameter is missing in the masthead, it is equivalent to setting the value 0.0.0.
- A BigFix 9.5.6 fresh installation, using a new License Authorization file, will automatically set this parameter to 9.5.6. BigFix 9.5.6 fresh installs using a masthead or license file, and any upgrade to 9.5.6 will not set this parameter.
Console Warning Message: “This message contains scripting and/or relevance.”
Starting from 9.5.6, an additional security check is performed by the BigFix Console every time new content is imported or created using a Console wizard or dashboard.
The new security check parses the content of the imported or generated fixlet/task to identify the existence of possible script content. If something is detected, the Console Operator is alerted with the following Warning Panel:
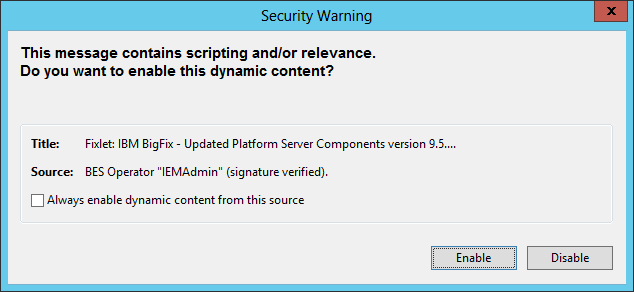
At this point the Console operator has 3 options:
- Trust the content for the specific fixlet/task by choosing the Enable Option (by choosing this option the user will still be prompted with the warning for new fixlets/tasks that contain scripting and/or relevance).
- Do not trust the current fixlet/task by choosing the Disable Option (by choosing this option the fixlet/task will be imported but the script content will be escaped).
- Trust the content coming from the specified Source for this and all future fixlets/tasks by selecting the checkbox “Always enable dynamic content from this source” and choosing the Enable Option (by choosing this option the user will not be prompted anymore while importing or generating new content from the trusted source).