Many organizations use Bitlocker to encrypt the hard drives of computers. This is typically done through a group policy requiring drive encryption and backing up the key to the Active Directory object. However, often times group policy is not available for remote users or unreliable due to the involvement of a VPN connection. With BigFix however, you can use Bitlocker with a series of steps to help you manage these remote workers and ensure that they are compliant with their drive encryption. Bitlocker requires you to have your TPM chip enabled and activated. Using a series of properties created by Strawgate, you can find candidates that have these settings enabled in the BIOS and encrypt the drive from BigFix. Strawgate also creates a method to store the Bitlocker key as a BigFix Property and view that data within the Console.
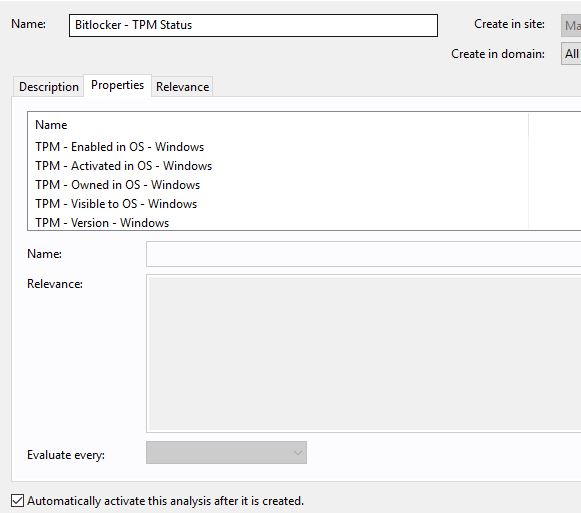
- Go to Bigfix.me and download the TPM – Status: https://bigfix.me/analysis/details/2998646
- Activate the analysis
This activates the TPM Analysis that provides valuable information.
Strawgate has created great content for Bitlocker for Windows 10:
- https://github.com/strawgate/C3-Protect/wiki/Bitlocker
- https://github.com/strawgate/C3-Protect/wiki/Bitlocker
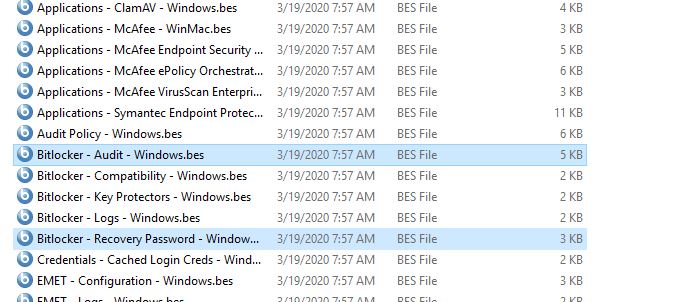
- Open the zip file it creates and open the analyses folder.
- Import the following into BigFix Console.
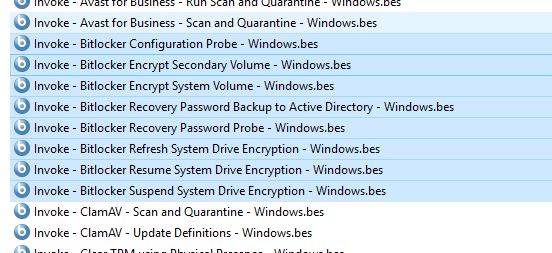
- Bitlocker - Audit - Windows.bes
- Bitlocker - Recovery Password - Windows.bes
- Go to the Fixlets section and import the following Fixlets into BigFix Console.
- Invoke - Bitlocker Configuration Probe - Windows.bes
- Invoke - Bitlocker Encrypt Secondary Volume - Windows.bes
- Invoke - Bitlocker Encrypt System Volume - Windows.bes
- Invoke - Bitlocker Recovery Password Backup to Active Directory - Windows.bes
- Invoke - Bitlocker Recovery Password Probe - Windows.bes
- Invoke - Bitlocker Refresh System Drive Encryption - Windows.bes
- Invoke - Bitlocker Resume System Drive Encryption - Windows.bes
- Invoke - Bitlocker Suspend System Drive Encryption - Windows.bes
You now have the content you need for gathering information about what PC’s are ready for encryption. The machines that can be encrypted are the ones that have their TPM chip enabled and activated.
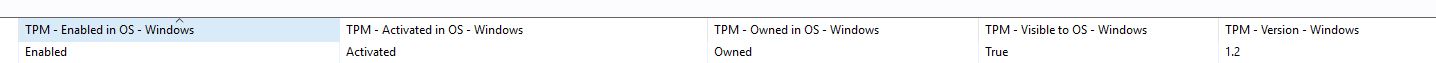
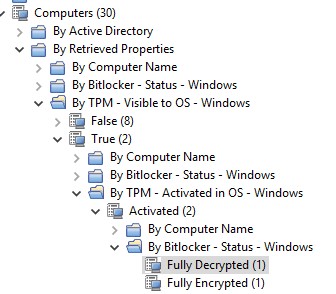
- Check the TPM – Status and then correlate that data with the machines that are still fully Decrypted.
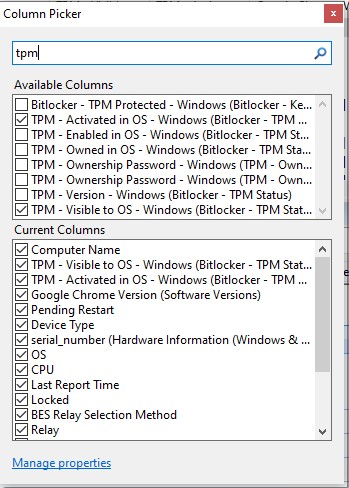
- In the Computers view in BigFix Console, add the properties:
- TPM – Activated in OS
- TPM – Visible to OS – Windows
- Bitlocker – Status - Windows
- Filter to display the PCs that are ready to be encrypted.
- TPM – Visible to OS – True
- TPM – Activated in OS – Activated
- Bitlocker – Status – Windows – Fully Decrypted
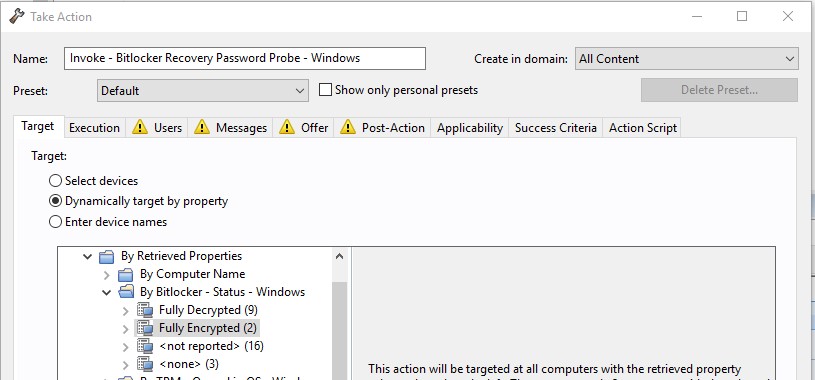
- Take action on the task Invoke – Bitlocker Encrypt System Volume – Windows on these PCs.
Note :Verify and test the action within your environment before deploying to multiple machines.
This encrypts the system drive of PCs.
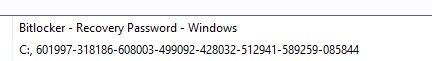
- Ensure that the key is backed up by creating a policy action for the task Invoke – Bitlocker Recovery Password Probe – Windows.
Once this probe runs, add your bitlocker key as a property in BigFix.
For machines that do not have TPM enabled or activated, enable each of these items by creating a package in BigFix. For instance Dell has a utility called Dell Command Configure that allows you to create packages to update the BIOS. Other manufactures have similar utilities. Following is a procedure that explains how to enable TPM chips and activate it on Dell machines.
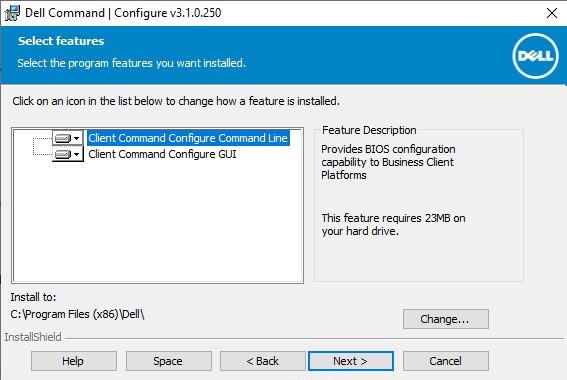
- Download and install the Dell Command Configure from http://downloads.dell.com/FOLDER03164404M/1
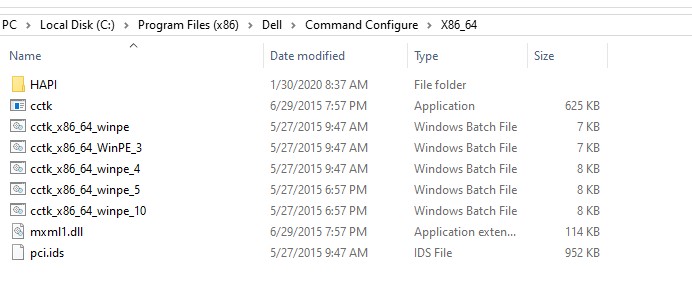
- Copy the files from C:\Program Files (x86)\Dell\Command Configure\X86_64 to a location from where you can upload them to BigFix
- In BigFix Console, go to the System Lifecycle domain.
- Click Software Distribution > Manage Software Distribution.
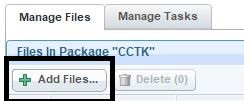
- Click New Package. Enter a name for the package.
- Add files to the package.
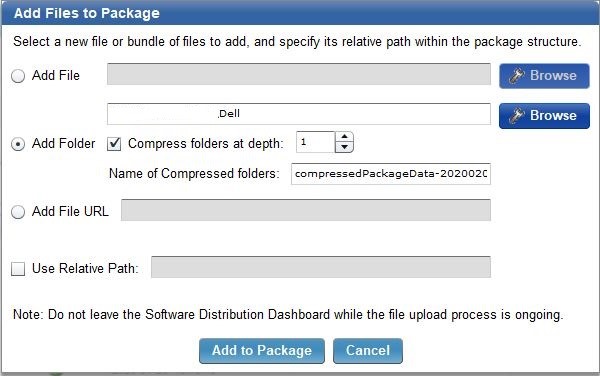
- Click Add to Package to add the folder you saved earlier with the Dell CCTK files.
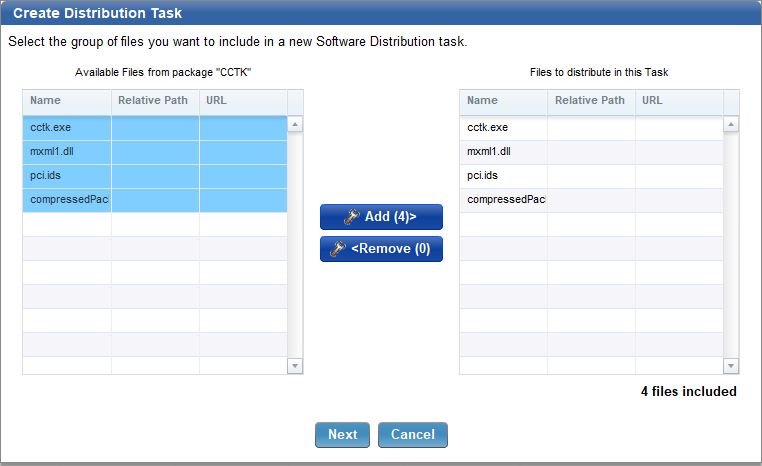
- Add the files.
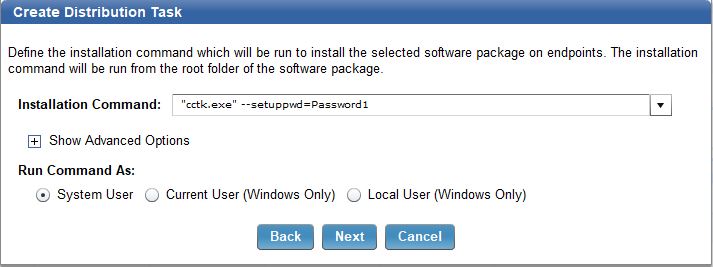
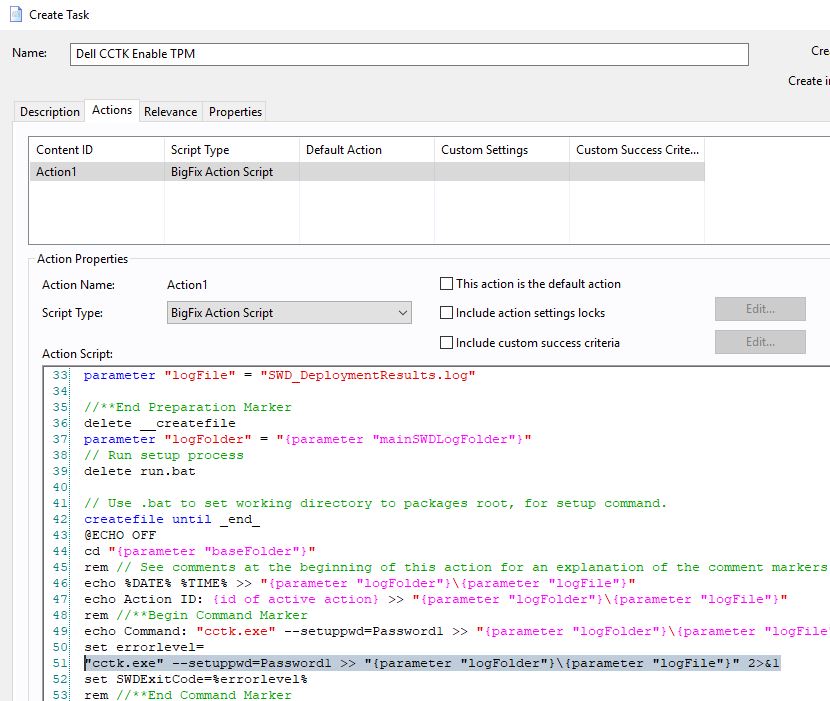
- Add the command "cctk.exe" --setuppwd=Password1 and click Next.
- Click Create Task
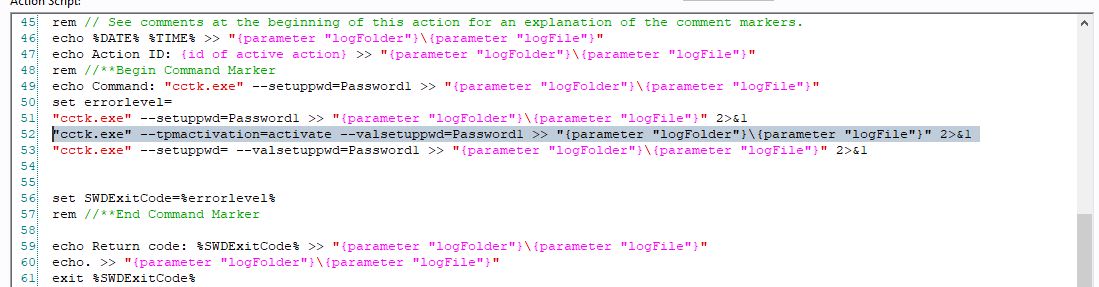
- Scroll down to line 51 and add two lines under the first command.
"cctk.exe" --tpm=on --valsetuppwd=Password1 >> "{parameter "logFolder"}\{parameter "logFile"}" 2>&1
"cctk.exe" --setuppwd= --valsetuppwd=Password1 >> "{parameter "logFolder"}\{parameter "logFile"}" 2>&1
The action script should look like this:
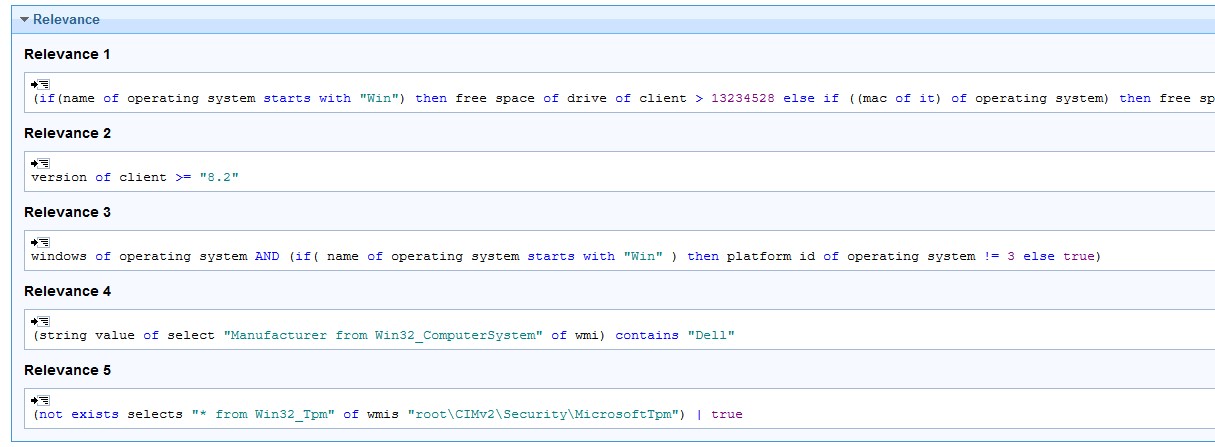
- Open the Relevance tab.
- Add the following statement to line 4:
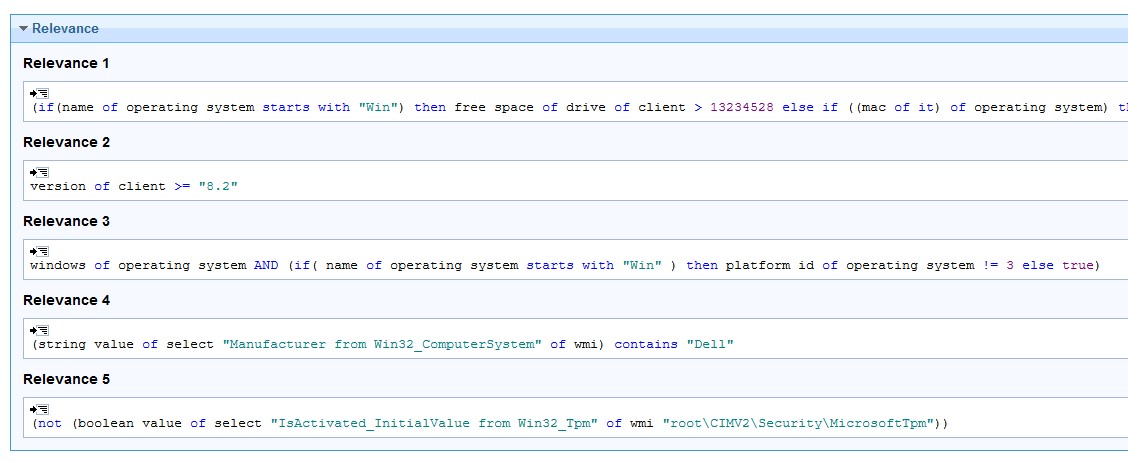
(string value of select "Manufacturer from Win32_ComputerSystem" of wmi) contains "Dell"
- Add the following statement to line 5:
(not exists selects "* from Win32_Tpm" of wmis "root\CIMv2\Security\MicrosoftTpm") | true
- Save the task.
- Create a copy of the task - click Copy.
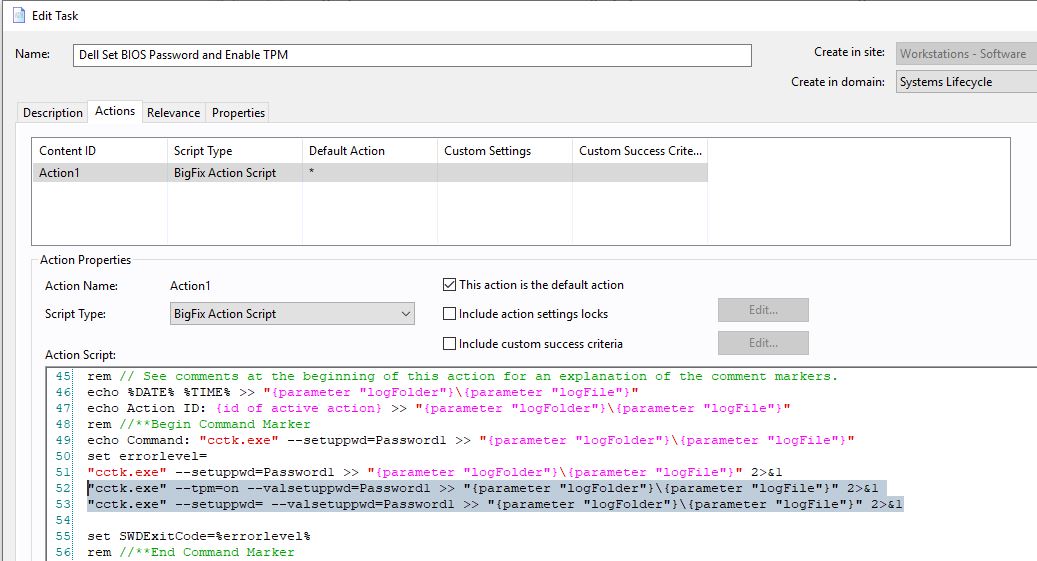
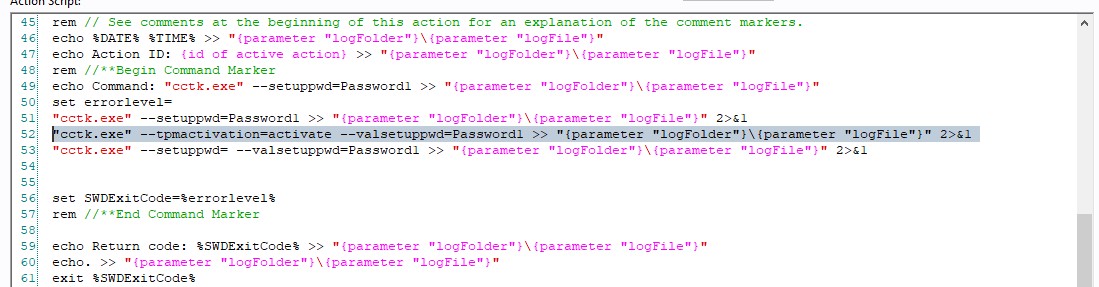
- Scroll down to the action script and edit the line 52.
- Replace the text on line 52 with the following text:
"cctk.exe" --tpmactivation=activate --valsetuppwd=Password1 >> "{parameter "logFolder"}\{parameter "logFile"}" 2>&1
Your action script should look like this:
- Open the Relevance tab.
- Add the statement to line 4.
(string value of select "Manufacturer from Win32_ComputerSystem" of wmi) contains "Dell"
- Add the statement to line 5.
(not (boolean value of select "IsActivated_InitialValue from Win32_Tpm" of wmi "root\CIMV2\Security\MicrosoftTpm"))
- Enter a name for the task. For example, "Dell Activate TPM' and save the task.
The task should look like this:
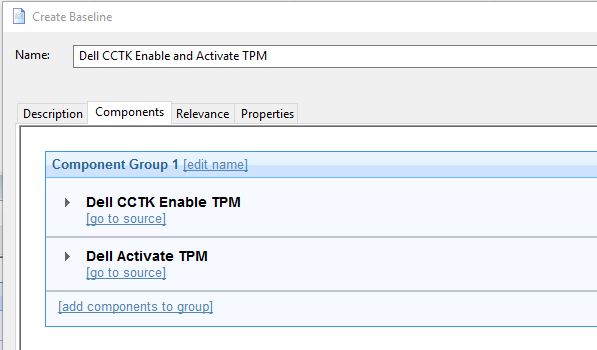
- Create a baseline with the two newly created tasks and save it.
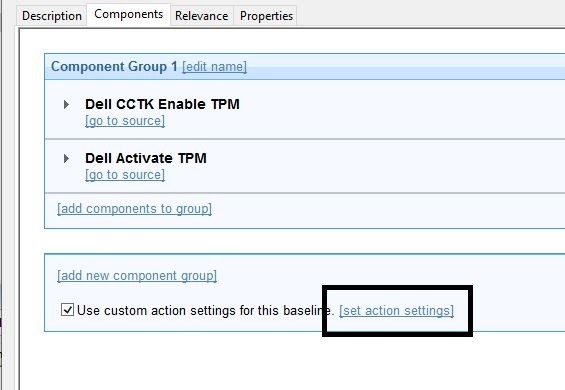
- Click set action settings for the baseline.
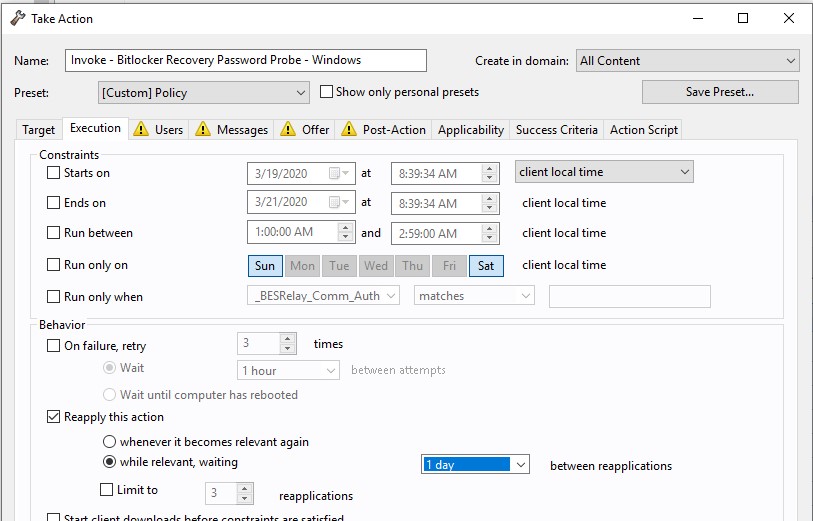
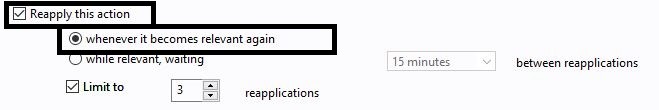
- Open the Execution tab and select the Reapply this action and whenever it becomes relevant again options.
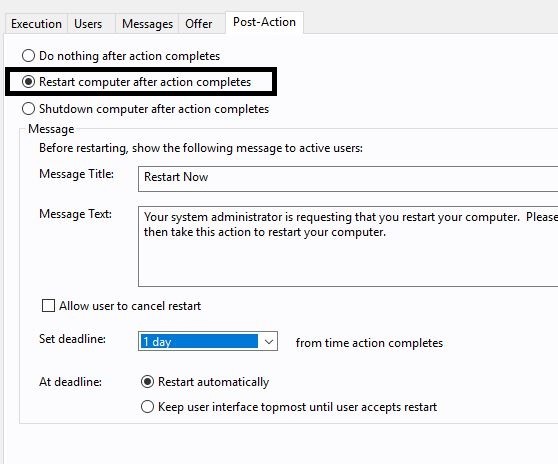
- Open the Post Action tab and select the Restart the computer after the action completes option.
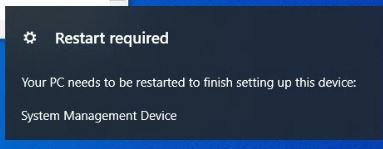
You can apply this action to any PC that does not have TPM Enabled or TPM Activated. This will enable TPM and if TPM does not activate, it will activate and prompt for a second reboot. You can now encrypt the drive with Bitlocker.
Note: Users may receive a prompt outside of BigFix that might ask them to restart their machine.
If by chance the TPM chip does not activate, it could be that the ownership needs to be cleared. Due to the TPM standards, this might require manual intervention.